A Framework for Scalable Detection Engineering in Microsoft Sentinel
Our SOC doesn’t just respond to alerts; we invest in proactive detection engineering and threat hunting to stay ahead of adversaries. Default rules are a good starting point, but without refinement, they often generate noise or miss key attack patterns.
As our client base has grown, we have focused on building repeatable and well-documented detection content. This ensures high-confidence alerts, stronger workflows for analysts, and a clear path for maturing our operations.
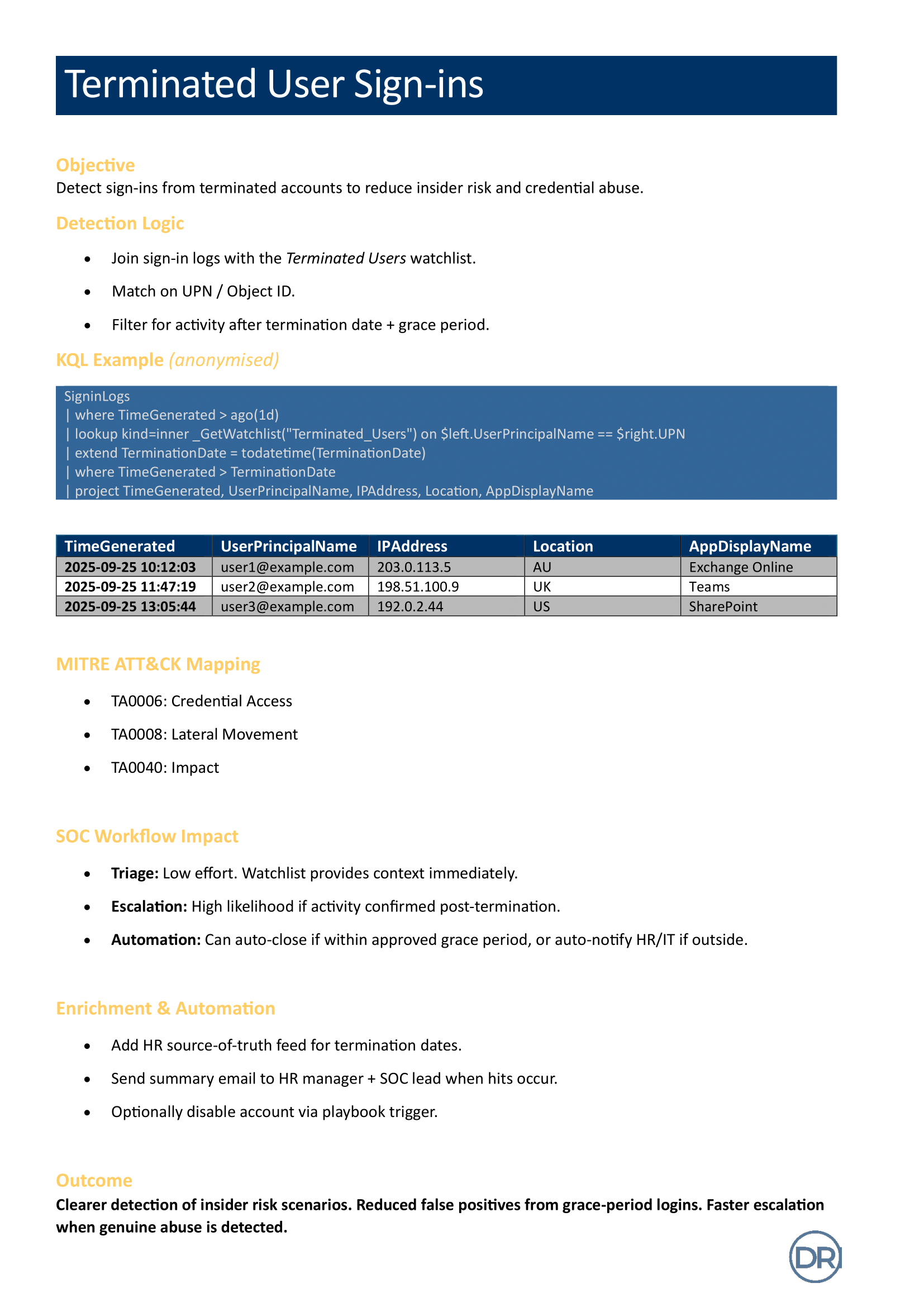
Over the past quarter, I developed a set of "one-pager" documents to capture and share our most valuable custom detections and hunting queries in Microsoft Sentinel. Each one includes:
The KQL query
Use case description
MITRE ATT&CK mapping
SOC workflow impact
Visuals or screenshots where useful
This framework has reduced time-to-value for new detections and empowered our SOC team to scale smarter.